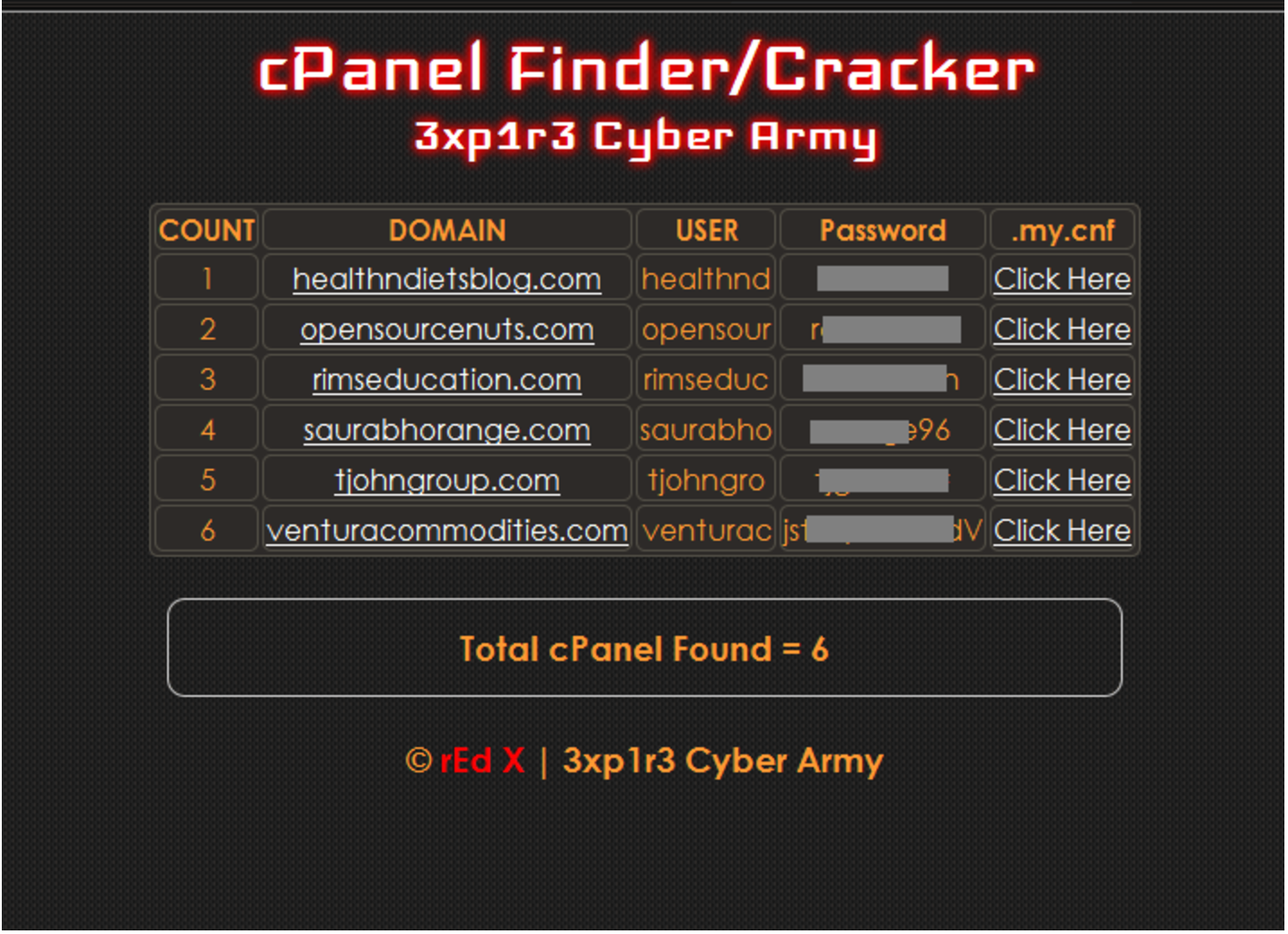
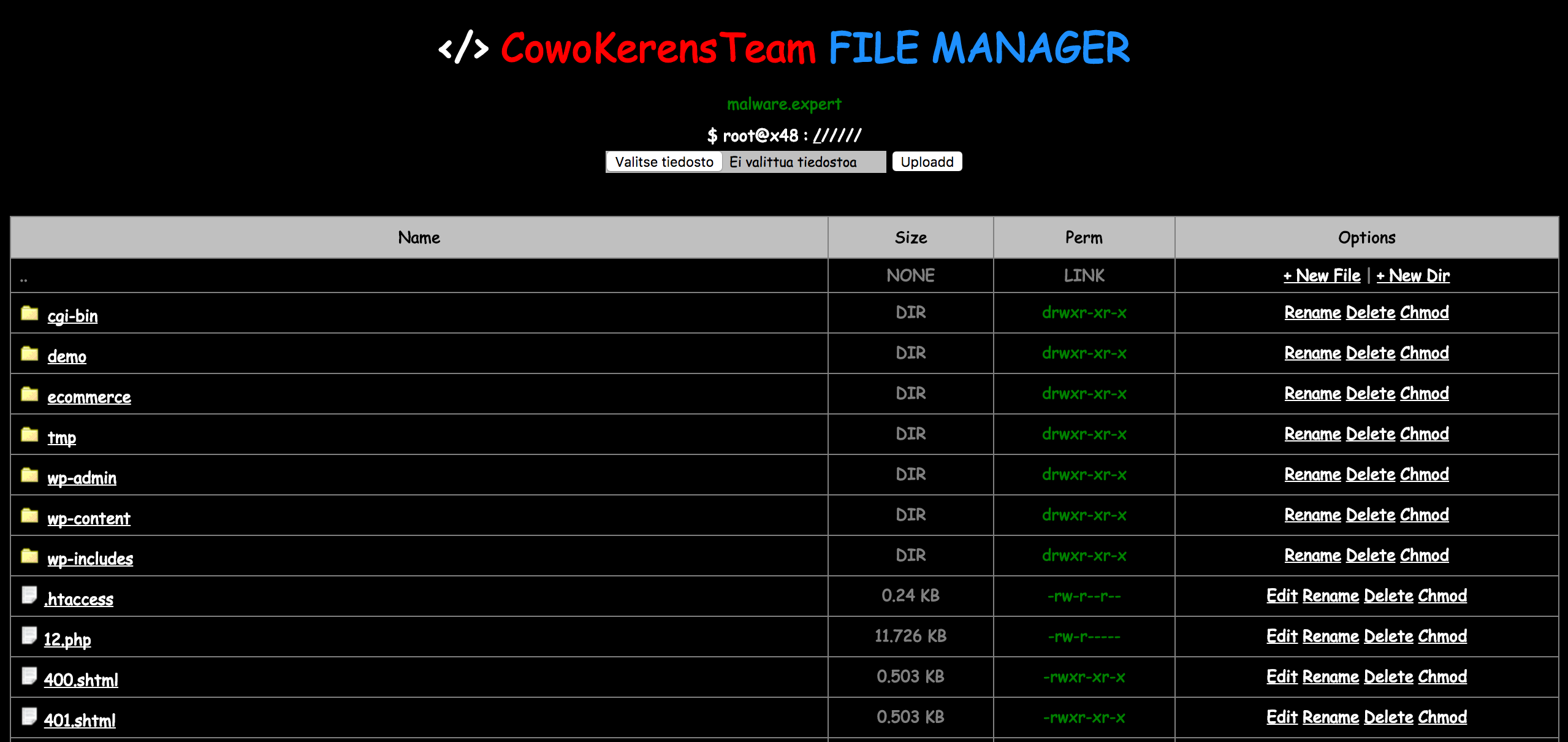
styles.php malware
Again, we found interesting malware (styles.php), which try to add more backdoor files to the web server. This file is just copied from the original file: load-styles.php. If you look fast this file, it’s look normal PHP file, but there is a modification of the begin (comments not finished line 6): It self hidden malware … Read more