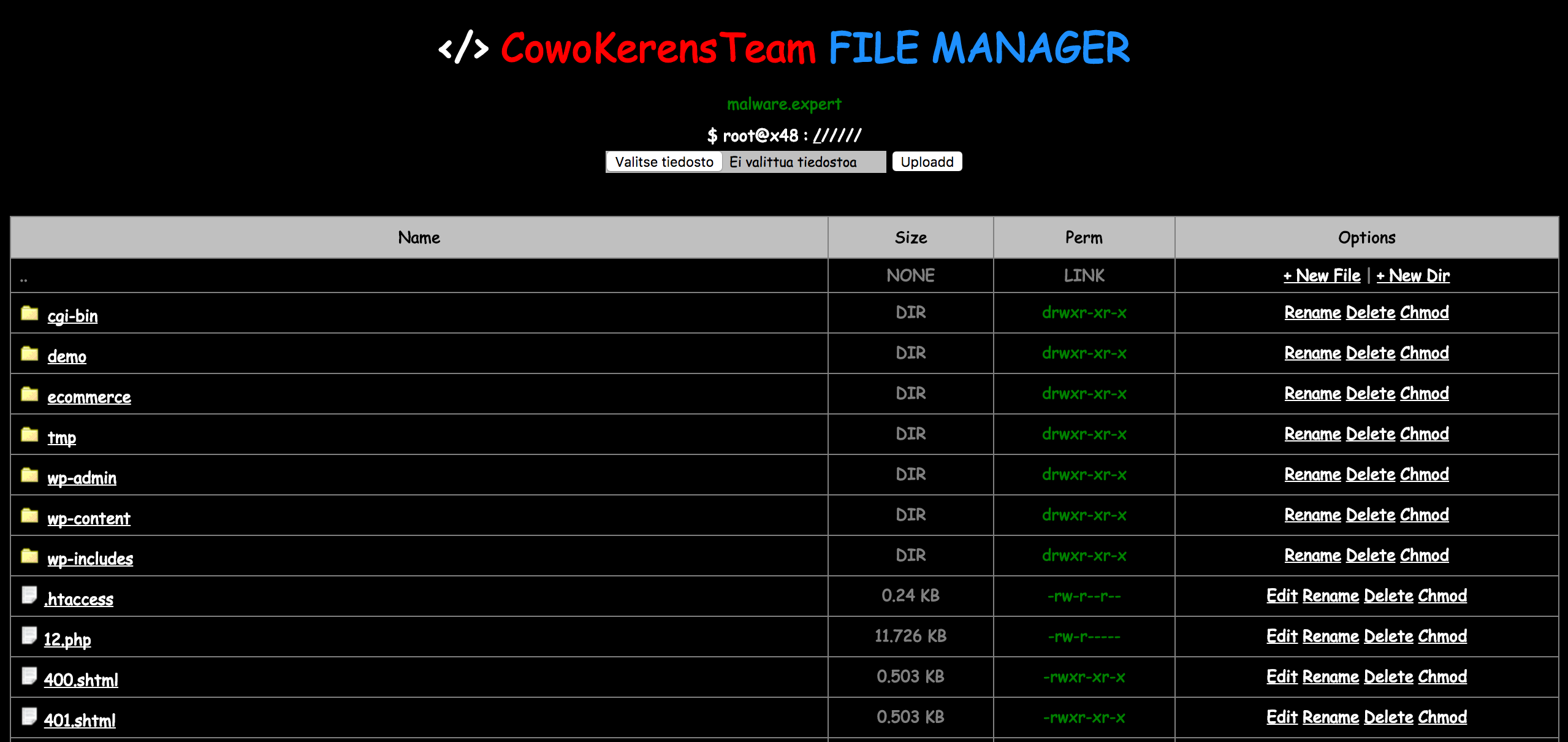
Malware plugin’s to WordPress (woocomerce & aksimet)
When WordPress website user account compromised, there is possibility upload plugins. We have seen new malware plugins for WordPress which are named with woocomerce and aksimet. These plugins not have anything doing with real plugins, which are woocommerce and akismet. Both of these plugins use WordPress add_action(‘init’,”) function to activate itself and ready take commands … Read more