wp-crawl.php
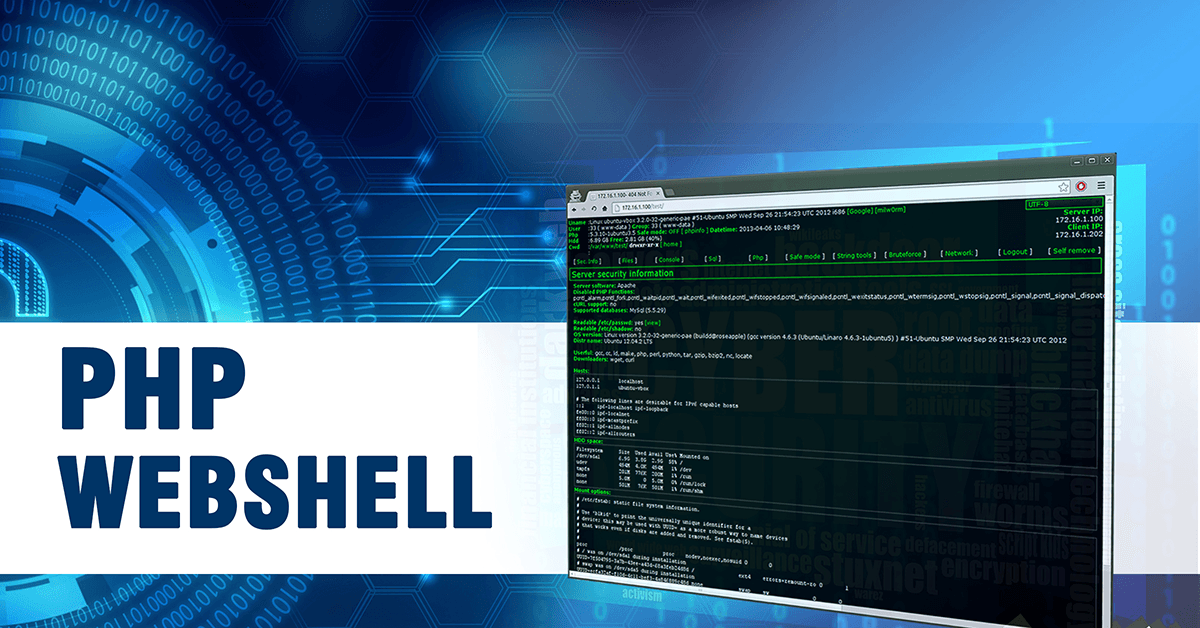
WordPress Duplicator version below <1.2.42 have Remote Code Execution (RCE) vulnerability, which allow modify wp-config.php file and inject malicious PHP code in there. Vulnerable code in this case isn’t present within the Duplicator plugin directory itself. The flaw becomes exposed when using Duplicator to migrate or restore a backed-up copy of a WordPress site. Reminder … Read more