WordPress hidden cookie (wp_cookie)
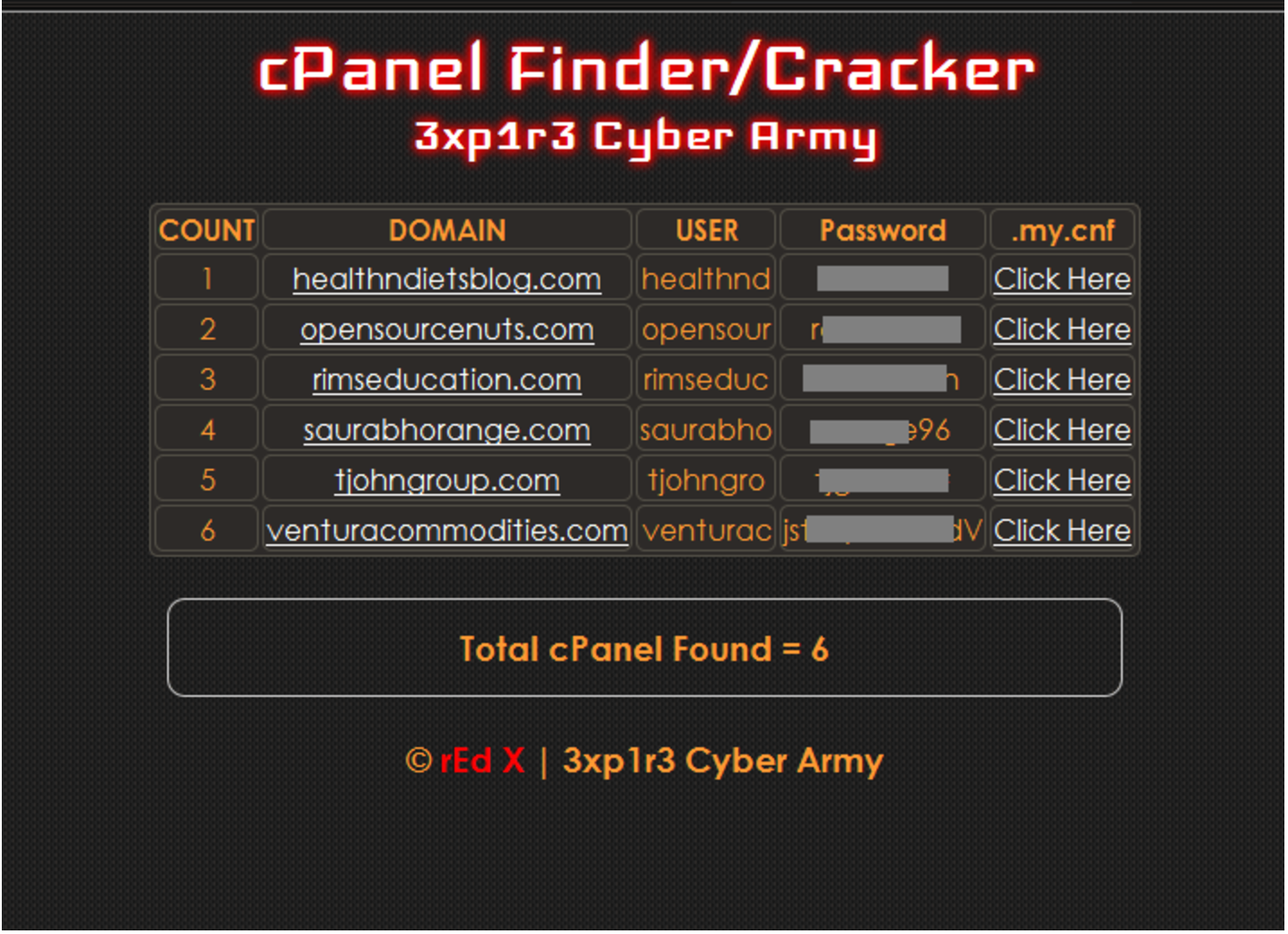
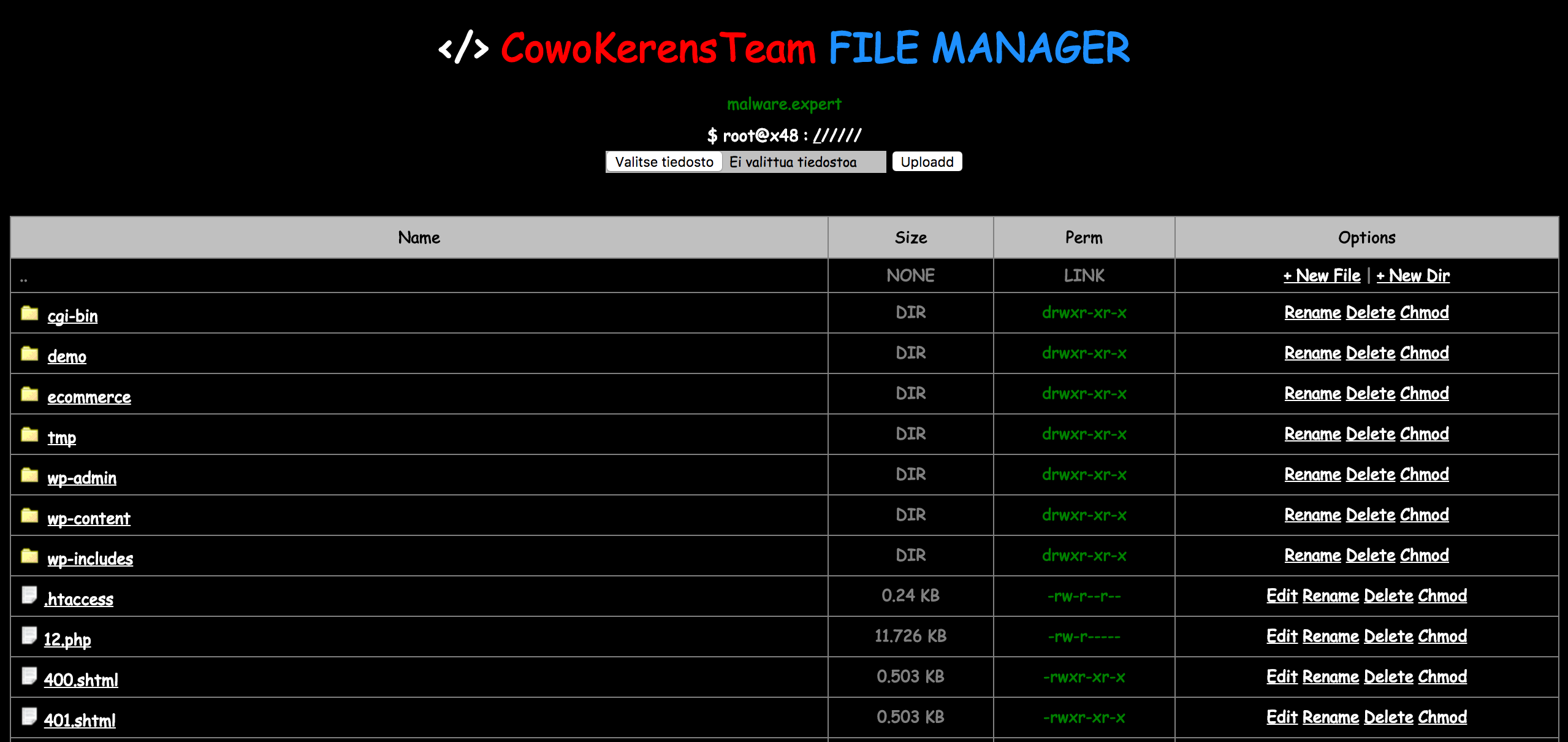
We found very old and hidden WordPress cookie, which named wp_cookie. This allows an attacker to run anything on the compromised user website with user permissions. wp_cookie This is a very clever attack method that allows arbitrary commands to run on a server with ignoring any server security software, just like normal PHP code. Also, … Read more