Ssh is the main tool/service used by a system administrator for doing the troubleshooting and other admin related tasks. If we have ssh root access, we can do anything on the server. So in order to keep the server secure, we need to follow some security practices related to ssh service. Since it is a critical service, we need to give extreme care while securing the server. Once the root ssh shell is comprised, then it is completed. We need to copy all data to another server after cleaning or from a working backup. As I said before, once we gain access to root, the hackers can add backdoors in the server, which can’t be identified by scanners too.
Use custom port for ssh
Default ssh port is 22 and there are lots of attacks come to that port. So as a security measure it should be changed to a non-standard port. By doing that we can avoid the attacks to ssh to a great extent. If your host is targeted, then the change in port will not help, they will find the ssh port in any other way. In the normal case, the attack will reduce by 90-95 % after changing the default port.
Please note, changing the port doesn’t mean that ssh is secure. Still, the service run on another port and the present vulnerabilities are still present unless it is patched well.
How to change ssh port
You need to login to the root console for updating the ssh port. Open the configuration file for the ssh service and edit the entry with “Port” and change the default port 22 to custom port based on the requirement. After editing the file restart ssh service and verify it is working.
Cofniguration file : /etc/ssh/sshd_config or /etc/ssh/ssh_config ( based on the distro )
Default entry;
Port 22
Note: While doing the ssh port change, make sure you will not be logged out from the current terminal before confirming everything is working fine, otherwise you will be kicked out from the server after closing the doors. In that case, we need to get console/IPMI access from the data center to bring back ssh into active. So take care while making changes to ssh. Do not attempt this unless you are qualified to do that.
Disable ssh root login
Disable root login via ssh and set an admin user with sudo access will get access to the root terminal for the administrators to do the server administration. In linux servers root is the admin user and it is known by all, so the hackers/crackers will attempt to login using root. So changing will add some security to the server. Also make sure to avoid using common names for the admin user like “admin”, “administrator” etc.
Set the following settings in ssh configuration to disable the root login.
PermitRootLogin no
Note: Before disabling root login, make sure you added admin user and added necessary privileges.
Disable password authentication
Once you disable the password authentication no user can login into ssh service using a password. All users need to configure ssh key for login. So before disabling the password authentication, the ssh key should be set up for your login. You can check the steps for setting up key-based authentication in linux or in the bottom of this article. After making the following changes to the ssh configuration restart the service to make the changes live.
PasswordAuthentication no
By disabling password authentication we can avoid the hacks due to the password breaking. By configuring the server firewall to block the IP from which the user trying wrong authentication method also will help to stop attacks.
Limiting ssh access by Users
Normally all system users can login into the server using ssh. We can limit the users by adding the users in the configuration file in the entries “AllowUsers” or “DenyUsers”
Limiting ssh access by IP
By limiting the access using IP will help to avoid attacks on the ssh service. You can use “/etc/hosts.allow” and “/etc/hosts.deny” files for limiting the access. Or using the system firewall to block the Port and only allow access to the specified ip’s
Security check for ssh configuration
You need to make sure the system packages ( here ssh ) is updated with the latest security patches. For centos based distros use “yum” and for debian based distros use “apt-get” or simply “apt” for updating the packages.
Setup ssh key authentication from Linux
First, we need to generate ssh key pair from the linux terminal of your linux desktop using the following command. It will ask for the key file needs to be saved, passphrase needed for the ssh key to be generated. Here I am not using any passphrase.
# ssh-keygen
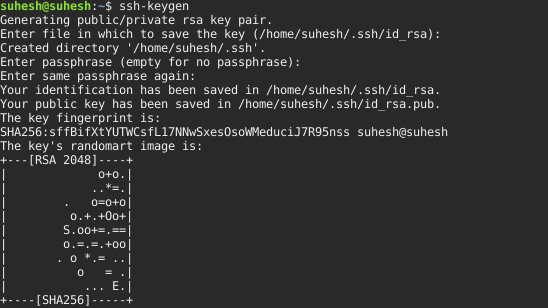
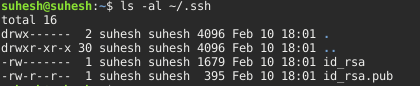
By default ssh private key is saved in ‘id_rsa’ file and public key in ‘id_rsa.pub’
Once the key pair is generated copy the public key and added it to the ‘authorized_keys’ file in the remote server in which we need to set up the key based login. Add the key by editing the file using any text editor or using the command ‘ssh-copy-id’.
~/.ssh/authorized_keys
# ssh-copy-id -i /path/to/public-key-file user@host
Conclusion
Even though we are enabling all the above options to secure the ssh, the chances of infection at our local end where the ssh key enabled and in that case access to the server, since we enabled ssh key authentication. One of the option to overcome this is to use passphrase while generating the ssh key pair. Normally we use a blank passphrase to avoid asking passphrase while trying to log in. Once we enabled passphrase, the login will ask for a passphrase and we need to enter the passphrase.

