ModSecurity works on a powerful language of rules and its API allows monitoring of HTTP(S) that is coming in and out of your web server, to keep your web applications up and running all the time.
This article is written to show how ModSecurity protects web applications running on Apache Web Server. The below diagram illustrates 5 processing phases of ModSecurity, implemented over a standard Apache web server request cycle.
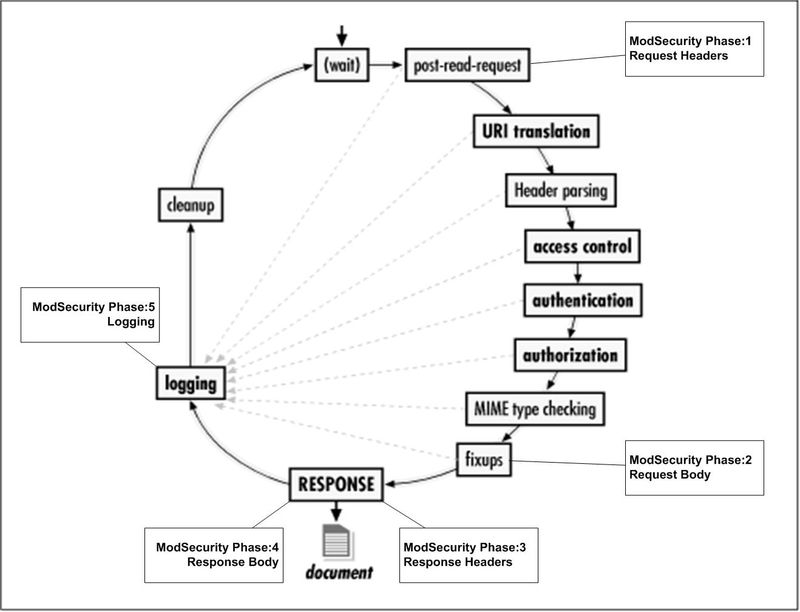
In these 5 phases, ModSecurity looks upon HTTP(S) data and analyzes it. These five phases are designed to provide a comprehensive shield of security.
ModSecurity Five phases are
- Request headers (REQUEST_HEADERS)
- Request body (REQUEST_BODY)
- Response headers (RESPONSE_HEADERS)
- Response body (RESPONSE_BODY)
- Logging (LOGGING)
Let’s have a detailed look at these stages.
Phase 1: Request Headers
This is the initial phase before Apache starts processing user requests. Rules in this phase read and analyze the HTTP Request Headers. The primary focus of rules in this phase is to see for malicious patterns in the Request Header before Apache starts processing the request arguments. Rules in this phase help in determining things like whether or not to buffer the Request Body, or how to process the Request Body (e.g. parse it as XML )
Phase 2: Request Body
After processing the Request Header, next in line is the Request Body. At this stage, Apache has received the complete request. Rules in this phase are mostly related to application.
ModSecurity supports the following three encoding techniques for this phase, these are almost used in every web server these days.
- application/x-www-form-urlencoded – for transferring form data
- multipart/form-data – for file transfers
- text/xml – for XML data
Phase 3: Response Headers
This is the phase where the Request has been processed and the Server starts sending back the requested data. Just like Request Headers rules, this stage rules see what in the Response Header is going back before sending the Response Body back to the user. Rules here help in deciding whether or not to buffer the Response body.
Phase 4: Response Body
Once the Response Request give a green signal to buffer the Response body, rules can be deployed to analyze what type of contents are going against each request. Here you can analyze Responses like Failed Authentication or Error messages.
Stage 5: Logging
This is the last part of the five-phase cycle which ModSecurity follows to secure your Apache. Rules in this phase are placed just before the actual logging takes place. In this phase log messages generated by the Apache web server are analyzed. One important thing about this phase is that you cannot block any connection here as it is after Request/Response phase. Here you can also inspect Headers that are not available during Phase 3 and 4.
Final words
After seeing the ModSecurity 5 Phases, it can be deduced easily that if you have deployed ModSecurity for Web Applications Security with Malware Expert – ModSecurity rules you have made the right decision.

