When a website gets hacked, one thing we know for sure is that attackers love to leave malware that allows them access back into the site in future. This type of malware is called a backdoor. This type of malware was named this because it allows for remote control of a compromised website in a way that bypasses appropriate authentication methods. You can update your site, change passwords, along with any of your admin procedures, and the backdoor would still be there allowing unexpected access to an attacker controlled everything usually user permissions.
Backdoors are also very hard to find because they don’t have to be linked directly in the website, they can be very small and be easily confused with “normal” code. Some of them have passwords, some are heavily encrypted/encoded and can be anywhere on your site, file system or database.
ini.php – Similar Filename Backdoors
The attacker will type website url – http://malware.expert/ini.php and a password will be requested (that by itself is very suspicious):
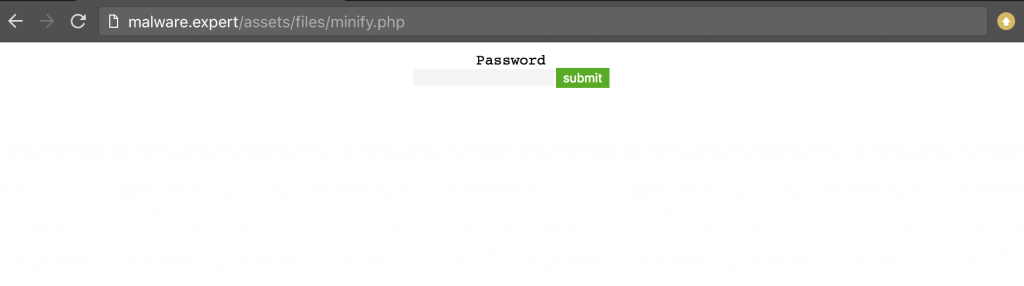
If you provide the correct password, it will display the backdoor dashboard with all of your files and many options to upload, rename, delete, inject malicious code and deface your website. Yes, that’s the Backdoor that is hidden inside that file:
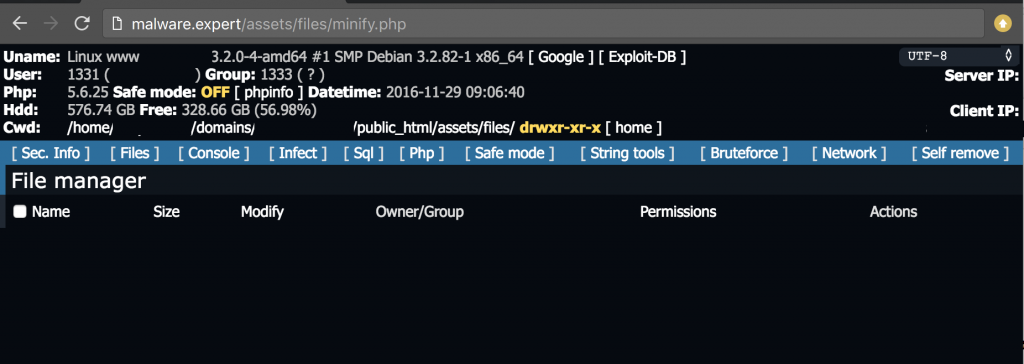
Protecting and Detecting Backdoors
As you can see, I recommended use more then one method to detect and protect by mixing modsecurity rules, waf firewall, ids firewall, blacklisting, scanning maldet with malware.expert – malware signatures and manual analysis to find all the backdoors on a website.
If you are trying to clean a compromised site by yourself, we recommend if possible delete all files and put back clean files. But if this not possible, then overwriting all the files you can (core files, plugins, etc). Of what is left, you have to manually analyze all the files to make sure they are clean.
Good tool scanning malware Maldet / Clamav & Our Signatures.
If you can’t get away all PHP malware, backdoor and etc, your site will be hacked again!
