php.ini
Securing cpanel php.ini in controlpanel or manually.
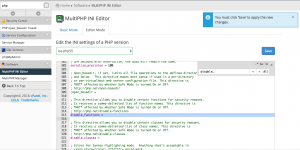
Login cpanel control panel and goto: Home » Software » MultiPHP INI Editor
Find disable_functions:
Change “disabled_functions =” to:
disable_functions = exec,system,passthru,shell_exec,escapeshellarg,escapeshellcmd,proc_close,proc_open,dl,popen,show_source,posix_kill,posix_mkfifo,posix_getpwuid,posix_setpgid,posix_setsid,posix_setuid,posix_setgid,posix_seteuid,posix_setegid,posix_uname
Or manually change files below:
# /opt/cpanel/ea-php55/root/etc/php.d/local.ini # /opt/cpanel/ea-php56/root/etc/php.d/local.ini # /opt/cpanel/ea-php70/root/etc/php.d/local.ini
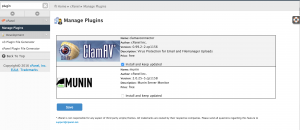
Install ClamAV Scanner
To install or uninstall ClamAV Scanner, use WHM’s Manage Plugins interface (Home » cPanel » Manage Plugins).
Offical Ducumentation Install ClamAV Scanner to Cpanel
ClamAV signatures
Edit Freshclam.conf file:
[root@cpanel]# nano -w /usr/local/cpanel/3rdparty/etc/freshclam.conf
Add these line end of file:
DatabaseCustomURL http://cdn.malware.expert/malware.expert.ndb DatabaseCustomURL http://cdn.malware.expert/malware.expert.hdb DatabaseCustomURL http://cdn.malware.expert/malware.expert.ldb DatabaseCustomURL http://cdn.malware.expert/malware.expert.fp
Restart Freshclam
[root@cpanel]# /usr/local/cpanel/3rdparty/bin/freshclam restart
Extra Signatures
if you want use more signatures to ClamAV, i suggest use Linux Malware Detect – www.rfxn.com
If you dont wanna install itself software, you can tweak and use only signatures to ClamAV. Add freshclam.conf end of file:
DatabaseCustomURL http://cdn.rfxn.com/downloads/rfxn.ndb DatabaseCustomURL http://cdn.rfxn.com/downloads/rfxn.hdb
ClamAV to ModSecurity
Edit file modsec2.user.conf :
[root@cpanel]# nano -w /etc/apache2/conf.d/modsec/modsec2.user.conf
Add begin of File:
SecRule FILES_TMPNAMES "@inspectFile /usr/local/bin/runav.pl" \ "phase:2,t:none,block,msg:'Virus found in uploaded file',id:'399999'"
Create File runav.pl:
[root@cpanel]# nano -w /usr/local/bin/runav.pl
Content of runav.pl file:
#!/usr/bin/perl
#
# runav.pl
#
# This script is an interface between ModSecurity and its
# ability to intercept files being uploaded through the
# web server, and ClamAV
# Fix clamdscan path to correct!
$CLAMDSCAN = "/usr/local/cpanel/3rdparty/bin/clamdscan";
if ($#ARGV != 0) {
print "Usage: runav.pl <filename>\n";
exit;
}
my ($FILE) = shift @ARGV;
$cmd = "$CLAMDSCAN --stdout --no-summary $FILE";
$input = `$cmd`;
$input =~ m/^(.+)/;
$error_message = $1;
$output = "0 Unable to parse clamscan output [$1]";
if ($error_message =~ m/: Empty file\.?$/) {
$output = "1 empty file";
}
elsif ($error_message =~ m/: (.+) ERROR$/) {
$output = "0 clamscan: $1";
}
elsif ($error_message =~ m/: (.+) FOUND$/) {
$output = "0 clamscan: $1";
}
elsif ($error_message =~ m/: OK$/) {
$output = "1 clamscan: OK";
}
print "$output\n";
Remember CHMOD 755
Restart:
[root@cpanel]# service restart clamd
ALso need modify ModSecurity configuration again:
[root@cpanel]# nano -w /etc/apache2/conf.d/modsec/modsec2.user.conf
Add these lines begin of file:
### Malware.Expert - ModSecurity rules ## CPanel configuration # SecComponentSignature "ME WAF" SecResponseBodyAccess Off SecDefaultAction "phase:1,deny,log,status:406" SecDefaultAction "phase:2,deny,log,status:406" SecRemoteRulesFailAction Warn SecUploadDir /tmp SecTmpDir /tmp SecUploadFileMode 0644 # Needed to ClamAV scan SecTmpSaveUploadedFiles on SecRequestBodyAccess On
Malware Expert – ModSecurity rules
Now full and final modsec2.user.conf edited file:
### Malware.Expert - ModSecurity rules ## CPanel configuration # SecComponentSignature "ME WAF" SecResponseBodyAccess Off SecDefaultAction "phase:1,deny,log,status:406" SecDefaultAction "phase:2,deny,log,status:406" SecRemoteRulesFailAction Warn SecUploadDir /tmp SecTmpDir /tmp SecUploadFileMode 0644 # Needed to ClamAV scan SecTmpSaveUploadedFiles on SecRequestBodyAccess On SecRule FILES_TMPNAMES "@inspectFile /usr/local/bin/runav.pl" \ "phase:2,t:none,block,msg:'Virus found in uploaded file',id:'399999'" SecRule REQUEST_METHOD "POST" "id:'400010',phase:1,t:none,chain,drop,noauditlog,msg:'Malware host detected by rbl.malware.expert'" SecRule REMOTE_ADDR "@rbl rbl.malware.expert" SecRemoteRules SerialKey https://rules.malware.expert/download.php?rules=generic
Note:
And replace SerialKey with your subscription serial key!
If you dont have Malware Expert ModSecurity rules, you can buy here.
Finally restart apache:
[root@cpanel]# service httpd restart