Last week, two cybersecurity companies found a Zero-Day vulnerability in WordPress SMTP Plugin. The vulnerability is located in the new import/export functionality added in v1.3.9 of Easy WP SMTP. It lets attackers exploit the lack of capability checks in the plugin’s admin_init hook to alter any values in the wp_options table.
Additionally, since the admin_init hook also executes in admin-ajax.php, the vulnerability can even be exploited by unauthenticated users. Therefore, anyone with sufficient know-how can easily modify the wp_user_roles field to set all user roles to “administrator”. Clearly, this is a huge issue. You can read an in-depth breakdown of how hackers are exploiting the vulnerability on the Wordfence blog or in this post by NinTechNet.
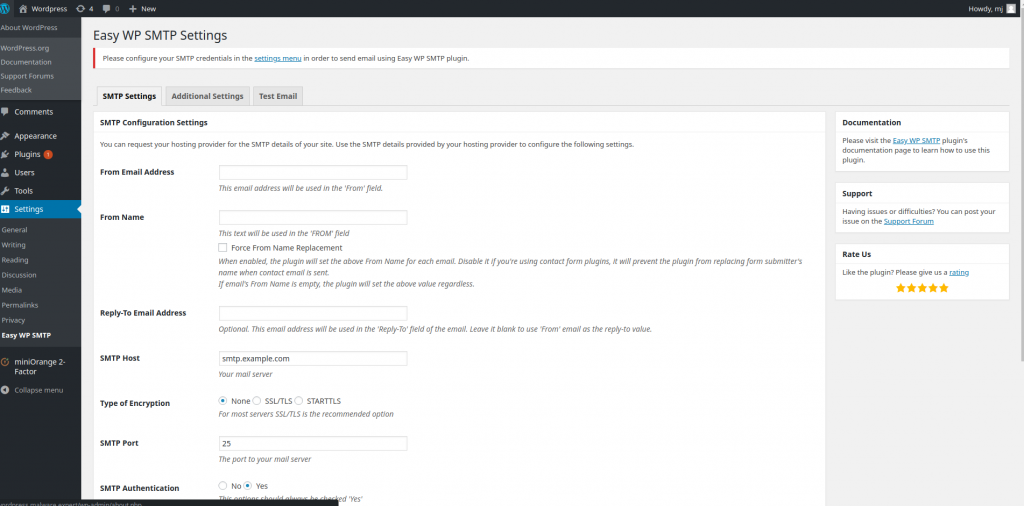
Easy WP SMTP allows you to configure and send all outgoing emails via an SMTP server. This will prevent your emails from going into the junk/spam folder of the recipients.
Moreover, 200,00+ active installs in WordPress websites and the vulnerability was first found by Ninja Technology and they reported the vulnerability to the authors and the wordpress.org team on March 15 and a new version 1.3.9.1 was released on March 17.
Link to the latest version of WordPress Easy WP SMTP plugin
If you are still using the old version of Easy WP SMTP then you should need to update 1.3.9.1 version.
- Check your WordPress “Settings > General” page: Make sure nothing was tampered with (URL, Email Address, Membership and New User Default Role).
- Check your WordPress “Users” page: Look for new users, weird admin accounts, check the admin email address etc.
- Change all passwords.
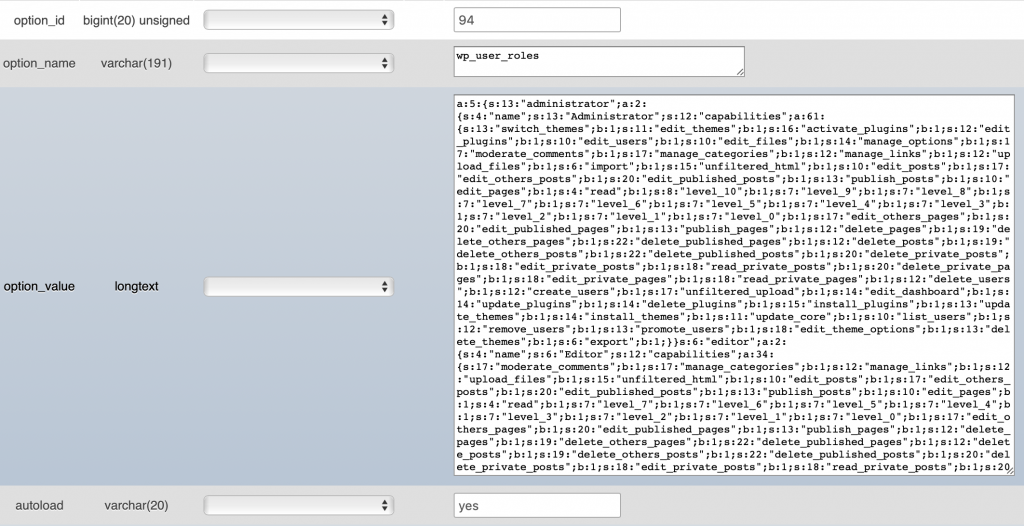
- Check your WordPress wp_options* table in the database”: Make sure wp_user_roles*, which contains user roles and capabilities, hasn’t been tampered with.
- Scan your files too, hackers may have uploaded backdoors.
- Change your SMTP password, hackers may have stolen it.
- Install a web application firewall with security rules to protect your website